Designing AWS Environments
By Wayde Gilchrist $31
https://www.udemy.com/designing-aws-environments
He's at www.packtpub.com - Seems mostly to be books.
Section: 1 - Installation and Setup
1. The Course Overview -- 3:08
linkedin.com/in/waydegilchrist (1)Focuses on EC@ Security Group Rules to protect them Windows and Linux Networking CIDR Notation Public and Private IP Addresses Create VPCs High Availability (2)VPC is for Isolation and Security
2. Opening an AWS Account -- 2:56
What can you do for free after 1 year?
3. The Free Tier -- 1:48
There is a lot of Free stuff... HSould probably keep track Always Free ... 25 Gig in Dynamo Db 10 Alarms in Cloud Watch 10 Gig In log data
4. The Management Console -- 2:36
There are two ways to login. Your account and password or as an IAM User. You can drag services to the upper task bar on the Console page. Billing, IAM, CloudFront, Route 53 do not need a region.
Section: 2 - Launching an EC2 Instance
5. Amazon Machine Images - EC2 -- 5:05
Stopping Instance storage You can restart EBS Instances and the data is retained...
6. EC2 Instance Types -- 5:12
This has some nice descriptions of the different instances and their configurations General Purpose Compute Optimized Memory Optimized GPU Optimized Stoprage Optimized All use Xeon processors. Micro Instances use Burstable CPU (only ones that do) T2 . the 2 is a generation version. *** Select to enable Public IP
7. EC2 Storage Options -- 7:54
Instance Storage - SSD Data is wiped when stopped so that the slot in the Hypervisor is cleared Do not put important data in Instance Storage! Size varies a lot depending on Instance Type. Boot Volumes, Temp/Swap files, Replicated data, Stateless Applications Using instance Storage means to create and AMI, you need to copy the files to S3 first - called Bundling.. Cannot stop, only terminate No Full Volume Encryption Block Storage - Elastic Block Storage Durable Block storage Seperate lifecycle from Instance, so persiste when stopped. Use with EBS Optimized Instances (Is also mirrored) Volume Size 1GB - 16 TB. Can have multiple ones attached to EC2 Snap Shots (in S3) and Full Volume Encryption Provisioned EBS have set (high) IOPS throughput.
8. Security Groups -- 4:59
Security Group is necessary for an instance Make firewall routes By default, all inbound routes are blocked. Repsonses to requests will all be allowed - Stateful Changes are instantaneous. Security Groups start with a default SSH rule. They start with a source of 0.0.0.0 which should be changed... to your IP or maybe the range of your office. Probably want to allow ALL 0.0.0.0. for HTTP and HTTPS. Now you need to use or create a new Key Pair for access. Download this.
Section: 3 - Logging in to EC2 Instances
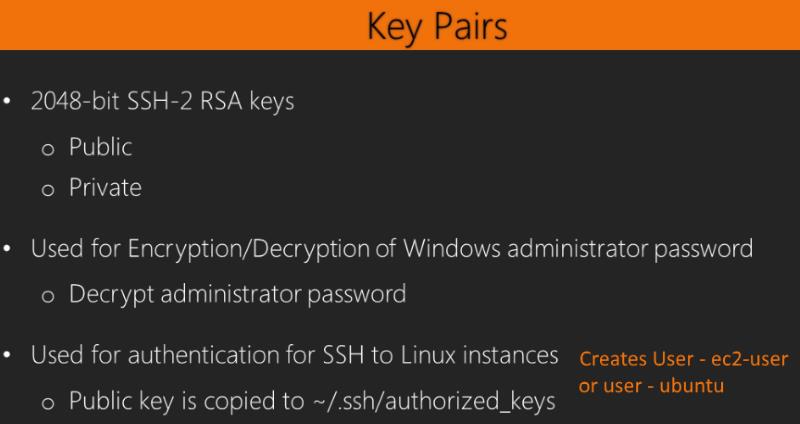
9. Key Pairs -- 3:06
You log into an EC2 Instance with a Key Pair
10. Logging in to Linux Instances -- 6:48
Pretty good description using SSH --- including about adding other users that can connect.
11. Logging in to Windows Instances -- 3:42
Using Remote Desktop You are going to need to make a security rule to allow connection with RDP. For a Mac connection, you need to get it from the Apple Store.
Section: 4 - Networking on AWS
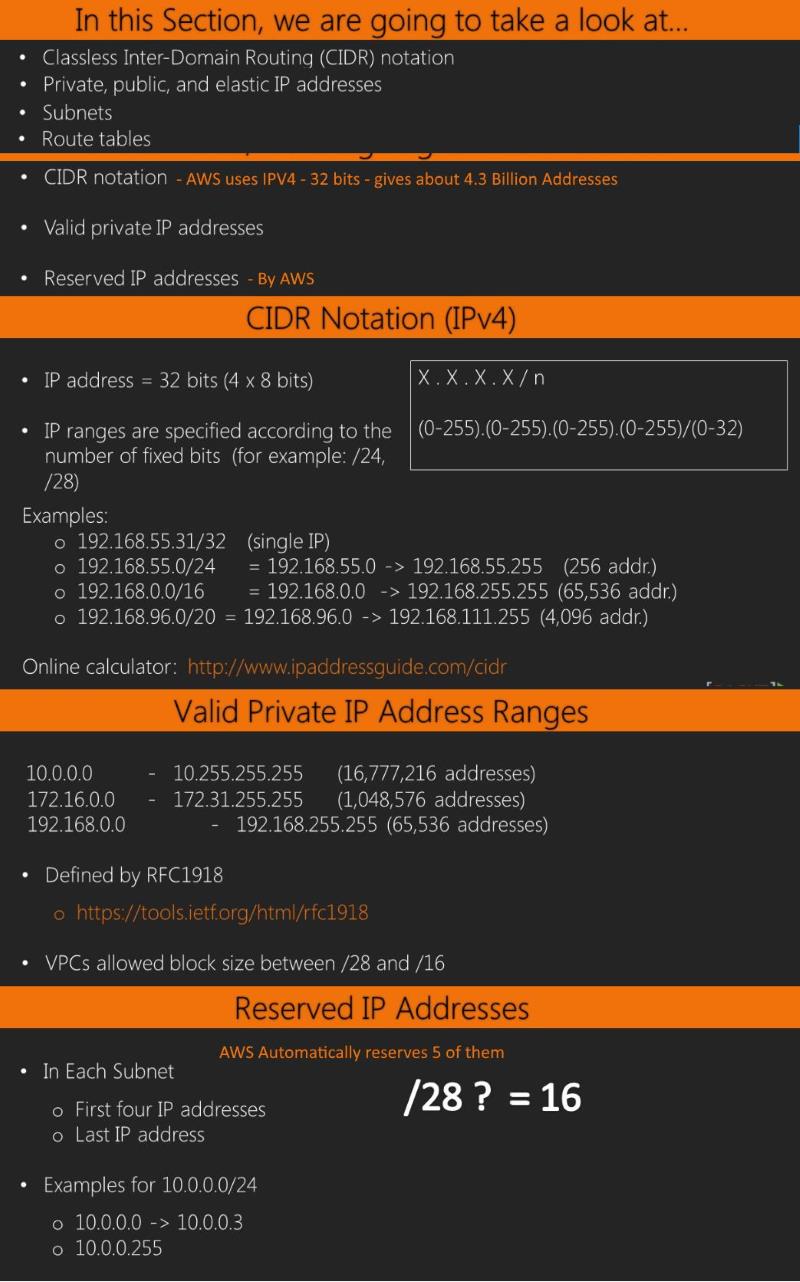
12. Classless Inter-Domain Routing CIDR-- 4:44
CIDR notation is for defining IP Address Blocks.
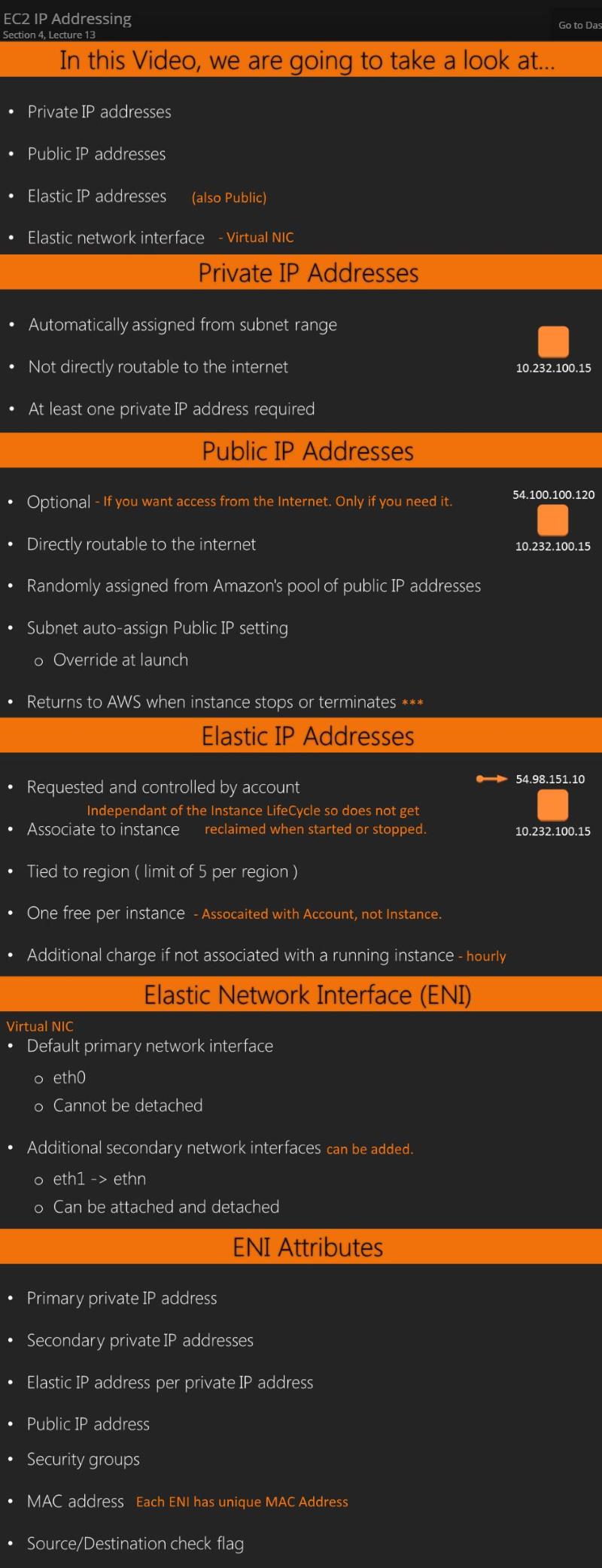
13. EC2 IP Addressing -- 6:04
14. Subnets and Route Tables -- 4:48
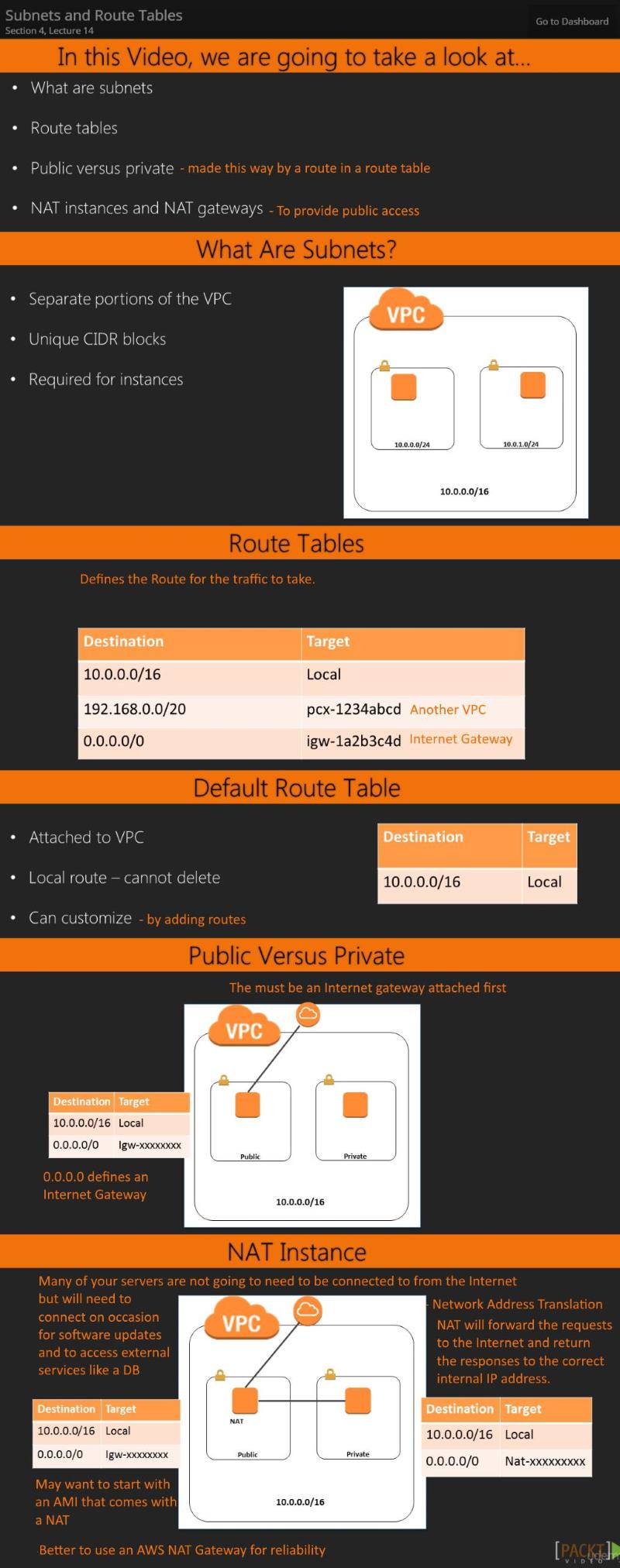
Section 5 - Creating a VPC
15. Getting Started with VPCs -- 7:12
This is really good... It's very like creating a Windows Domain with a Public and Private Subnet that is connected to the Internet. 1. Create VPC 2. Attach Internet Gateway 3. Create Public Address Block in VPC Block 4. Create Elastic IP from Subnet to Internet 5. Connect Public Subnet to Internet through Internet Gateway 6. Create Routing Table 7. Create Private Address Block in VPC Block 8. Create Route Table to VPC for Private Subnet Add Route from Internet (0.0.0.0)to the NAT Gateway Associate that Route Table with the Private Subnet 9. Connect Private Subnet to Internet through NAT
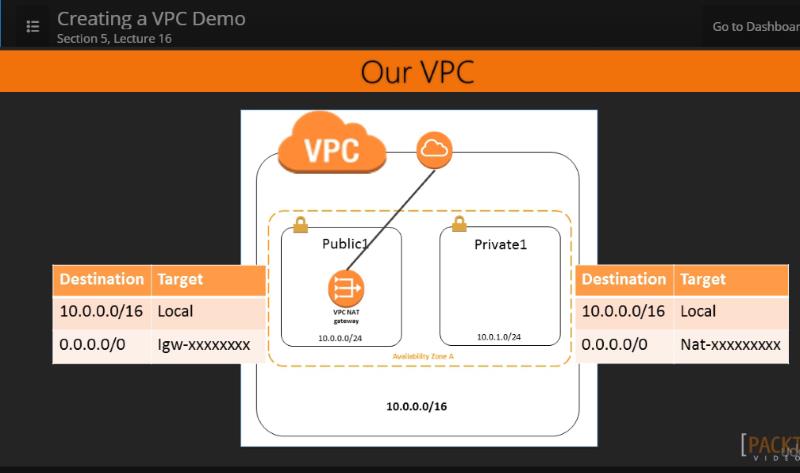
16. Creating a VPC Demo -- 9:07
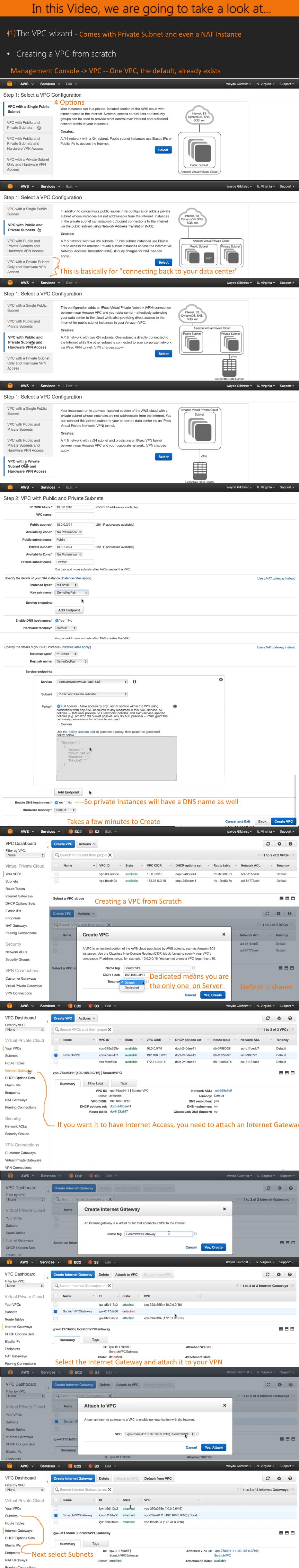
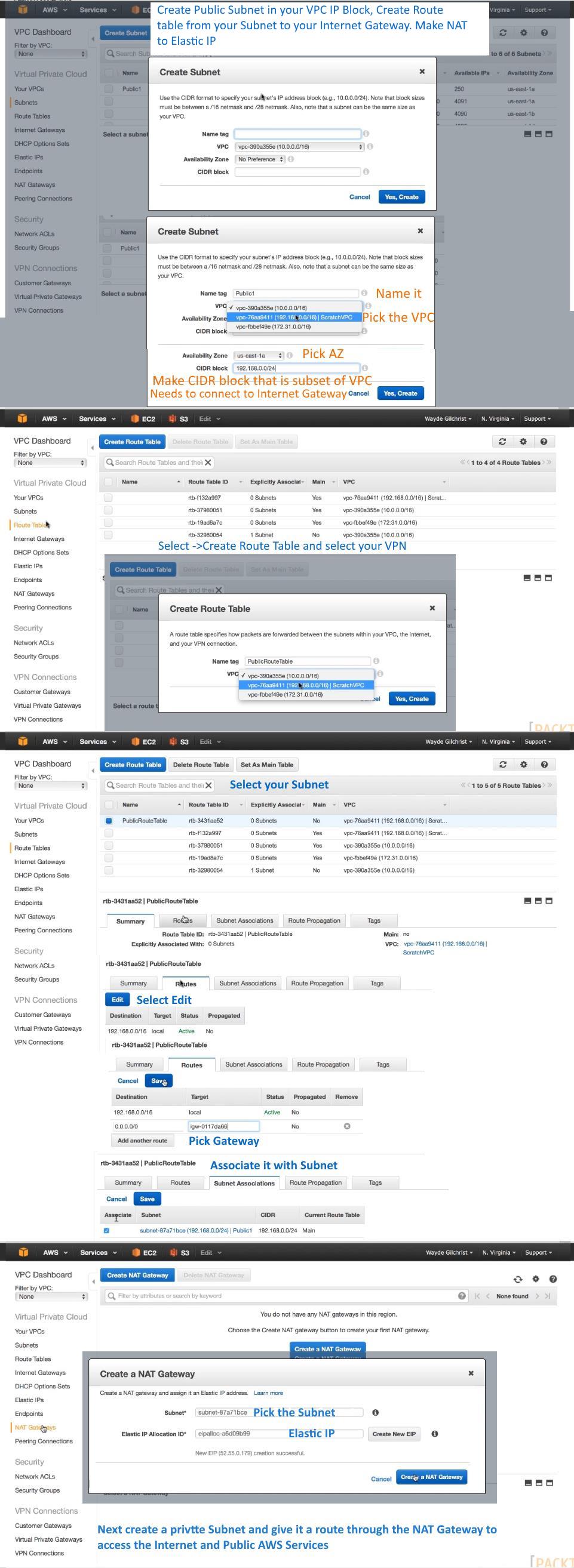
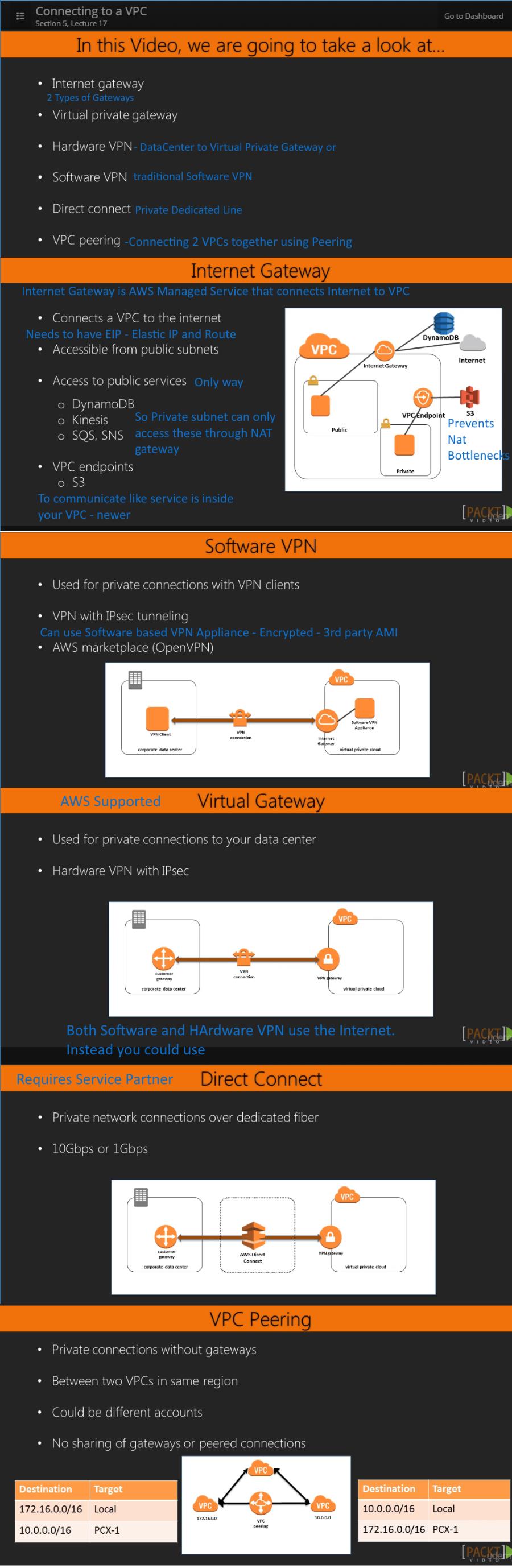
17. Connecting to a VPC -- 4:31
Using (1)VPN (2)Direct Connect
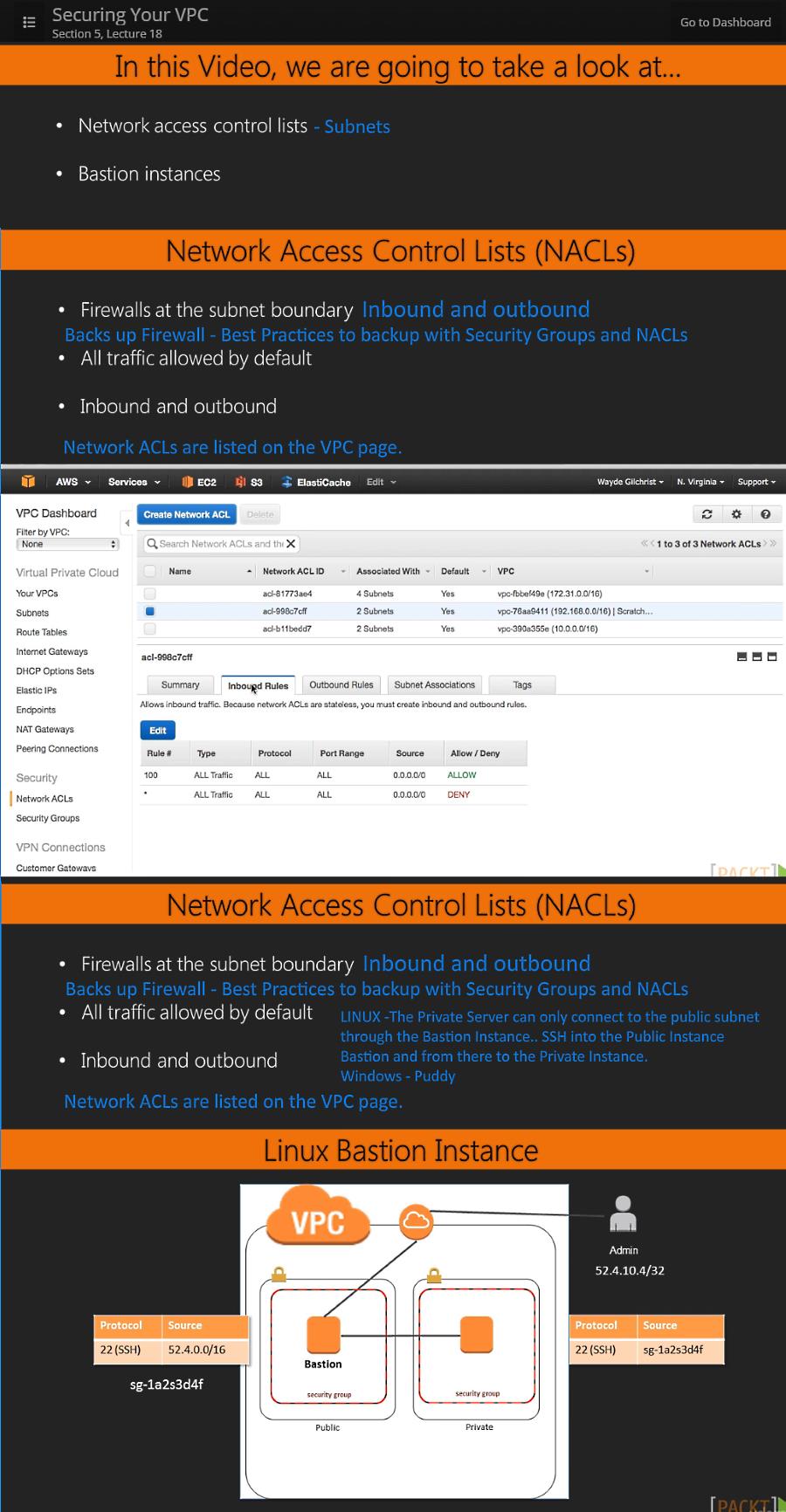
18. Securing Your VPC -- 12:29
This is about Robust network security. Best Practices.
(1) NACLs - Network Access Control Lists
They backup Firewalls and Security Groups by controlling address traffic.
Nice for services like Databases and such that are outside the VPC.
Stateless, so need both Inbound and Outbound rules.
(2) Bastions - Instances in Public subnets to protect backend App Servers
and Databases.Basically configured so that the Private Instance can only
be logged onto from the Bastion Instance.
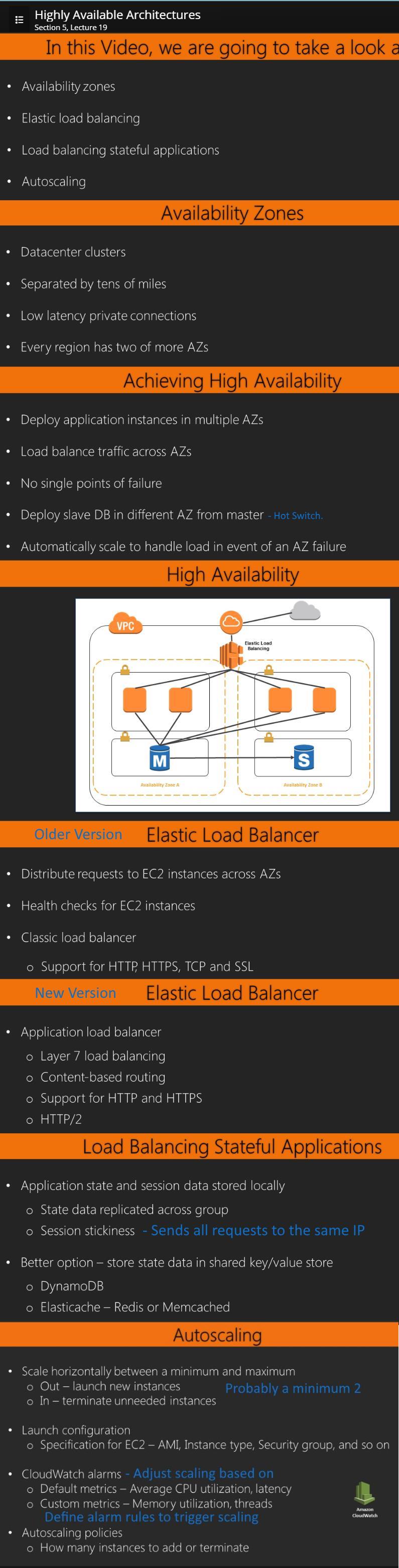
19. Highly Available Architectures -- 14:58
(1) Availability Zones - Deploy to multiple AZs. (2) Elastic Load Balancing (3) Load Balancing Stateful Applications (4) Autoscaling - He gives a detailed walkthrough of this configuration.